So you've played Watch Dogs and thought to yourself "that don't look too hard," and now you want to learn how to be a hacker. Well, you should know that there is more to hacking than just staring at your phone all day, which we all do anyway, and you have a long way to go if you want to give DEDSEC a run for their money.

Before we begin I should say up front that I am not a security expert and I may misrepresent certain details or skip over information as I oversimplify this topic for the sake of brevity. Feel free to chime in if I'm wrong about anything, or if I've glossed over something important.
To get a better insight into what it entails to be a hacker, you need to know what hacking is and what it isn't. "Hacking" is often used by the media as a catch-all term for any computer-related crime, but the crimes that can be committed using a computer are many and varied, so just calling everything "hacking" is a gross misunderstanding of how computers play a part in our connected world.
Real computer hacking is, at heart, exploiting the weaknesses in a computer system to gain access to protected data or features. It could mean probing a corporate network to get to company secrets or circumventing the software block on a console to make it run homebrew games. Whether this is done with malicious/criminal intent isn't exactly important, but die-hard hackers tend to prefer that the term "hacking" is reserved for exploiting weaknesses whereas "cracking" is the definition of hacking with the intent to steal, destroy, manipulate or commit some other crime (such as bypassing the DRM on a game, which is illegal under the DMCA).

Despite this distinction between innocuous and criminal hacking, there is still a separation in the hacking community between "good" and "bad" hacking, with the "white hat" and "black hat" monikers referring to the respective types. White hat hacking is hacking done for the sake of research or to test the security of a system, usually at the behest of the systems administrators, who are interested in how robust their system is in case they are targeted by others hackers (this is called penetration testing). Black hat hacking, on the other hand, is hacking done for selfish reasons, either to prove that you could, or because you have something to gain by exploiting the system. There are the obvious monetary gains, but some hackers are solely looking for a challenge or the infamy gained by breaking into heavily protected systems. They may notify the administrators of the system which they broke into to make them aware of the security hole, but unless actually invited to test the security of the system then this type of hacking isn't always appreciated (or legal). Where the line between this and "cracking" lies is subjective and the source of endless arguments, as is tradition in computer culture.
On a related side-note, it is impossible to talk about hacking without making a mention of phone phreaking. Phreaking was the 1960-1970s era phenomena of exploiting telephone systems by using specific frequencies of sound to trick the electronic switchboards into doing what you want. Most commonly it was to let you call long-distance for free, but it was also accompanied by a practice called "war dialling", which is a brute-force way of finding if there are any exploitable computer systems connected to the telephone network. Phreakers would gather in conference calls (for free), on unprotected corporate networks to trade stories, share techniques, and just hang out.
Despite all this talk about computer systems and program flaws, there is a much more analogue aspect to hacking which is important to mention. Most often, especially in this world of advanced firewalls and paranoid sysadmins, the weakest point in a system are the users. Hacking has always involved aspects of social engineering, where a hacker would convince another person to give them access to a private area or system, sometimes without doing anything more complicated than asking. We're naive and trusting creatures and our desire to help usually wins over any suspicions, especially if the person you're talking to seems legit.
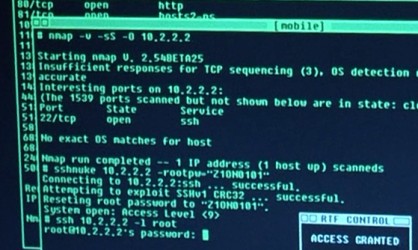
So you want to be a hacker? Meaning you want to exploit weaknesses in a computer system, and the humans using it, to gain access to information not meant for your eyes. Hacking itself is very difficult and involves a lot of research and experimentation which can take a lot of time to accomplish, especially when you're trying to exploit programming flaws or penetrate a well-constructed network. However, you can also find a lot of programs on the internet which exploit already-known flaws, giving you the powers to intrude into systems without all that hard work. But then you would be just a "script kiddie", and nobody likes script kiddies.
In the Watch Dogs game, Aiden Pierce is referred to as a great hacker but all he does is run programs on his phone which do the work for him. The game doesn't feature any of the poking and prodding that goes into actually finding weaknesses in secure systems and Aiden relies on the apps to do the heavy lifting. If you'd like a better example of hacking in a video game you should check out Uplink: Hacker Elite, which features a lot of techniques that real hackers use to exploit computer system. That way you can feel like the righteous hacker that you always wanted to be... but don't do any real hacking, though; that stuff is illegal.
Sources
- Hackaday
- DEFCON Conference talks
- The Art of Intrusion by Kevin Mitnick
- The Secret History of Hacking
- BBS: The Documentary
- Wikipedia and some small articles on Hacker News
Log in to comment